51% Attack
51% Attack: When Consensus Gets Hijacked
A 51% attack occurs when a single entity controls the majority of a network’s mining power or stake, allowing them to manipulate transactions and double-spend coins.
A 51% attack is when an individual or group controls more than half of a blockchain network’s mining hash rate or staking power, giving them the ability to reverse transactions and manipulate the blockchain. It’s the digital equivalent of hijacking the entire banking system.
How 51% Attacks Work
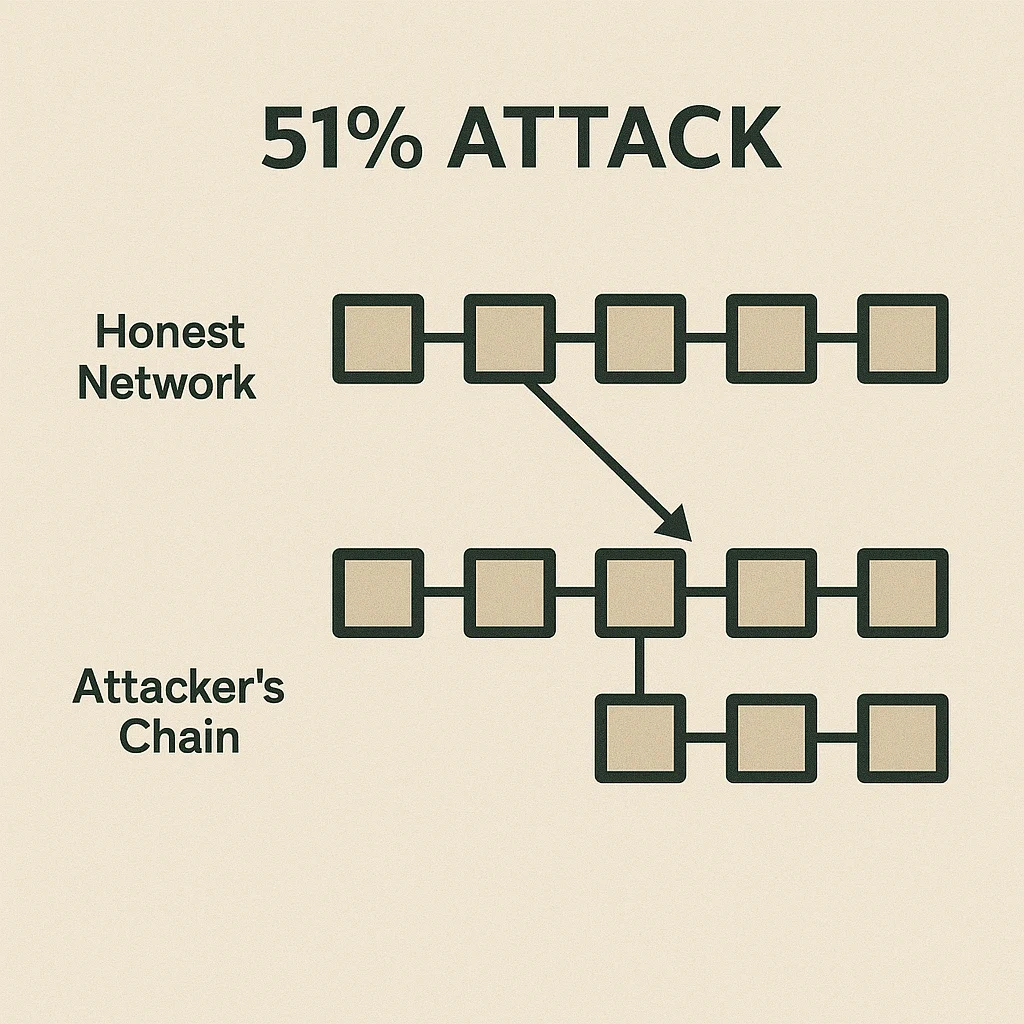
Majority control allows attackers to mine or validate blocks faster than the honest network, eventually creating a longer chain that becomes the “true” blockchain according to consensus rules.
Double spending becomes possible when attackers reverse their own transactions after receiving goods or services, effectively spending the same coins twice.
Network disruption can halt transaction processing as attackers refuse to include certain transactions in blocks or reorganize the blockchain to exclude them.
Real-World Examples
- Bitcoin Gold suffered multiple 51% attacks resulting in millions in double-spent coins
- Ethereum Classic experienced several attacks after major miners moved to Ethereum mainnet
- Smaller altcoins are frequent targets due to lower hash rates and cheaper attack costs
Why Beginners Should Care
Network size matters for security. Bitcoin’s massive hash rate makes 51% attacks prohibitively expensive, while smaller networks remain vulnerable to well-funded attackers.
Exchange risks increase during 51% attacks as attackers often target high-value transactions on exchanges through double-spending schemes.
Recovery challenges exist after successful attacks. Networks must decide whether to reverse attacker transactions, which can undermine immutability principles.
Related Terms: Hash Rate, Mining, Consensus Mechanism, Double Spending
