Public Key
Public Key: Your Crypto Receiving Address
Your public key is like your email address for crypto – you can share it freely without security concerns.
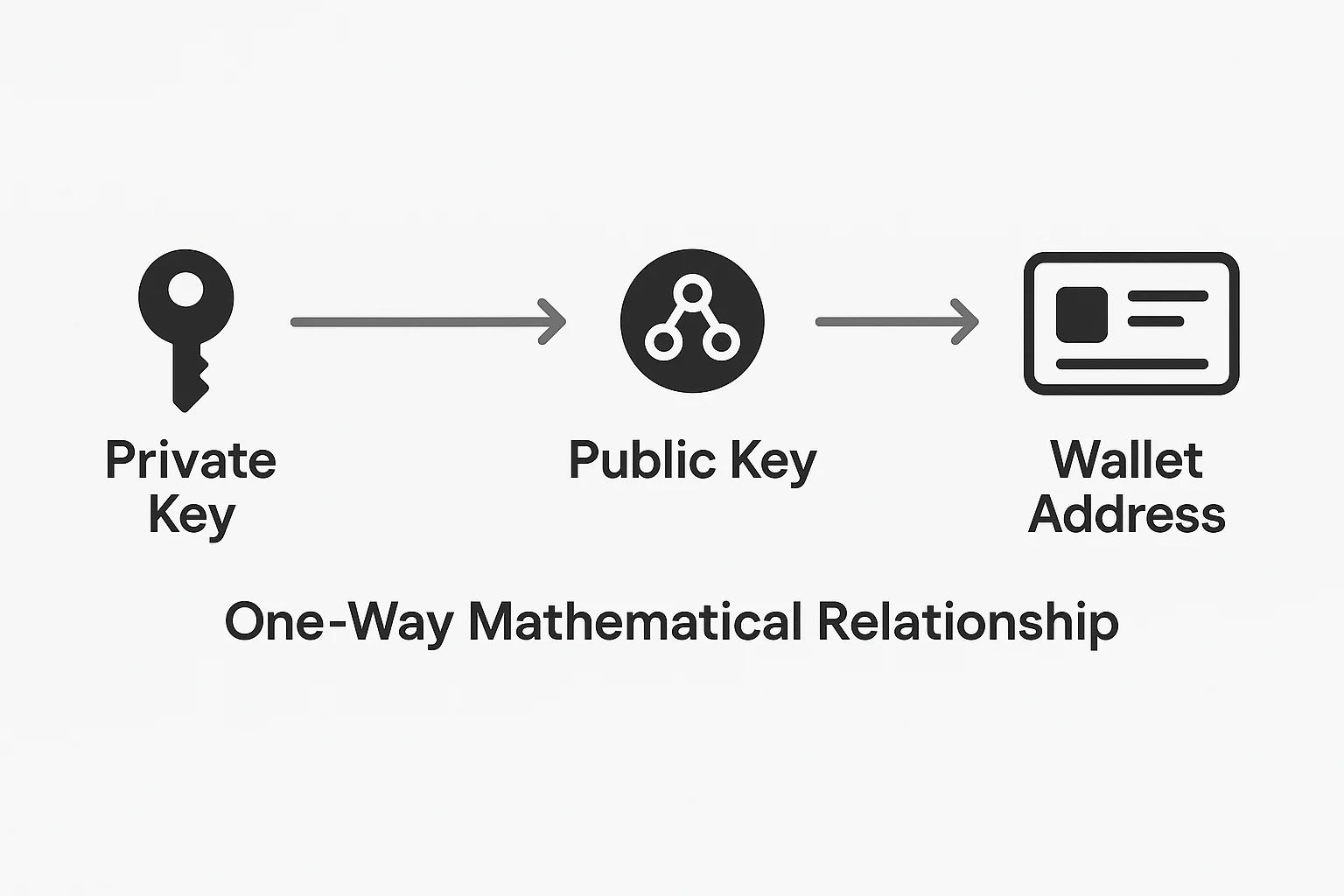
A public key is cryptographically derived from your private key and generates your wallet addresses where others can send you cryptocurrency. It’s mathematically linked to your private key but reveals nothing about it.
How Public Keys Work
Your private key mathematically generates your public key through one-way cryptographic functions. This public key then creates your wallet addresses.
Anyone can use your public key to verify that transactions were actually signed by your private key, but they can’t work backwards to discover your private key.
It’s like a mathematical lock that only your private key can open, but everyone can verify the lock belongs to you.
Real-World Examples
- Bitcoin addresses start with 1, 3, or bc1 and are derived from public keys
- Ethereum addresses are 42-character strings starting with 0x
- QR codes often encode public keys for easy mobile payments
Why Beginners Should Care
Understanding the private key/public key relationship helps you grasp crypto security fundamentals. Your public information (addresses) can be shared freely, while your private information (keys) must remain secret.
This cryptographic system enables trustless transactions. People can send you crypto without knowing anything about you except your public address.
Related Terms: Private Key, Wallet Address, Digital Signature, Cryptography
