Dusting Attack
Dusting Attack: Tracking Through Tiny Transactions
Dusting attacks send tiny amounts of cryptocurrency to addresses to track user behavior and deanonymize transactions. It’s like sprinkling digital breadcrumbs to follow where people go.
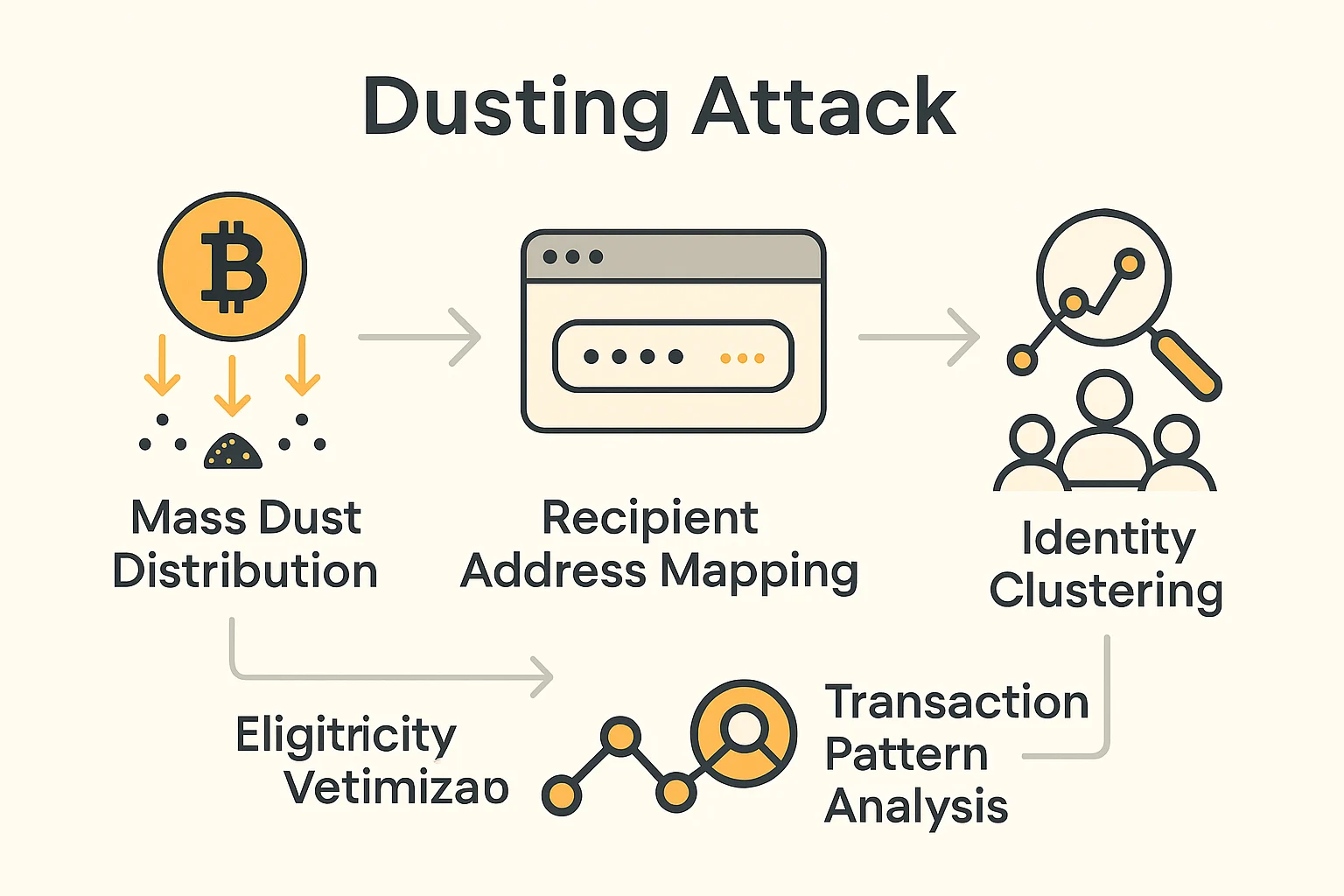
A dusting attack sends small amounts of cryptocurrency (dust) to many addresses to track users’ transaction patterns and potentially identify wallet owners. Attackers hope recipients will consolidate dust with other funds, revealing connections between addresses.
How Dusting Attacks Work
Mass distribution of tiny token amounts targets thousands of addresses simultaneously, often using automated tools to send minimal amounts that barely exceed network dust limits.
Behavioral analysis tracks how recipients handle dust, looking for patterns like consolidation with main balances or specific timing that reveals user habits.
Address clustering connects multiple addresses to single users when dust gets mixed with other transactions, potentially deanonymizing previously private holdings.
Real-World Examples
- Bitcoin dusting campaigns have targeted hundreds of thousands of addresses with minimal satoshi amounts
- Binance Smart Chain tokens often used for dusting due to extremely low transaction costs
- Privacy coin attacks attempt to break anonymity features through sophisticated dusting techniques
Why Beginners Should Care
Privacy erosion occurs when dust gets mixed with legitimate transactions, potentially revealing spending patterns and wallet connections to surveillance companies.
Wallet hygiene practices include freezing or ignoring dust rather than spending it, preventing attackers from gaining additional tracking information.
Limited direct harm exists from dusting attacks themselves – they don’t steal funds but can compromise privacy if handled improperly.
Related Terms: Privacy, Address Clustering, Transaction Analysis, Anonymity
