Sandwich Attack
Sandwich Attack: Extracting Value from Your Trades
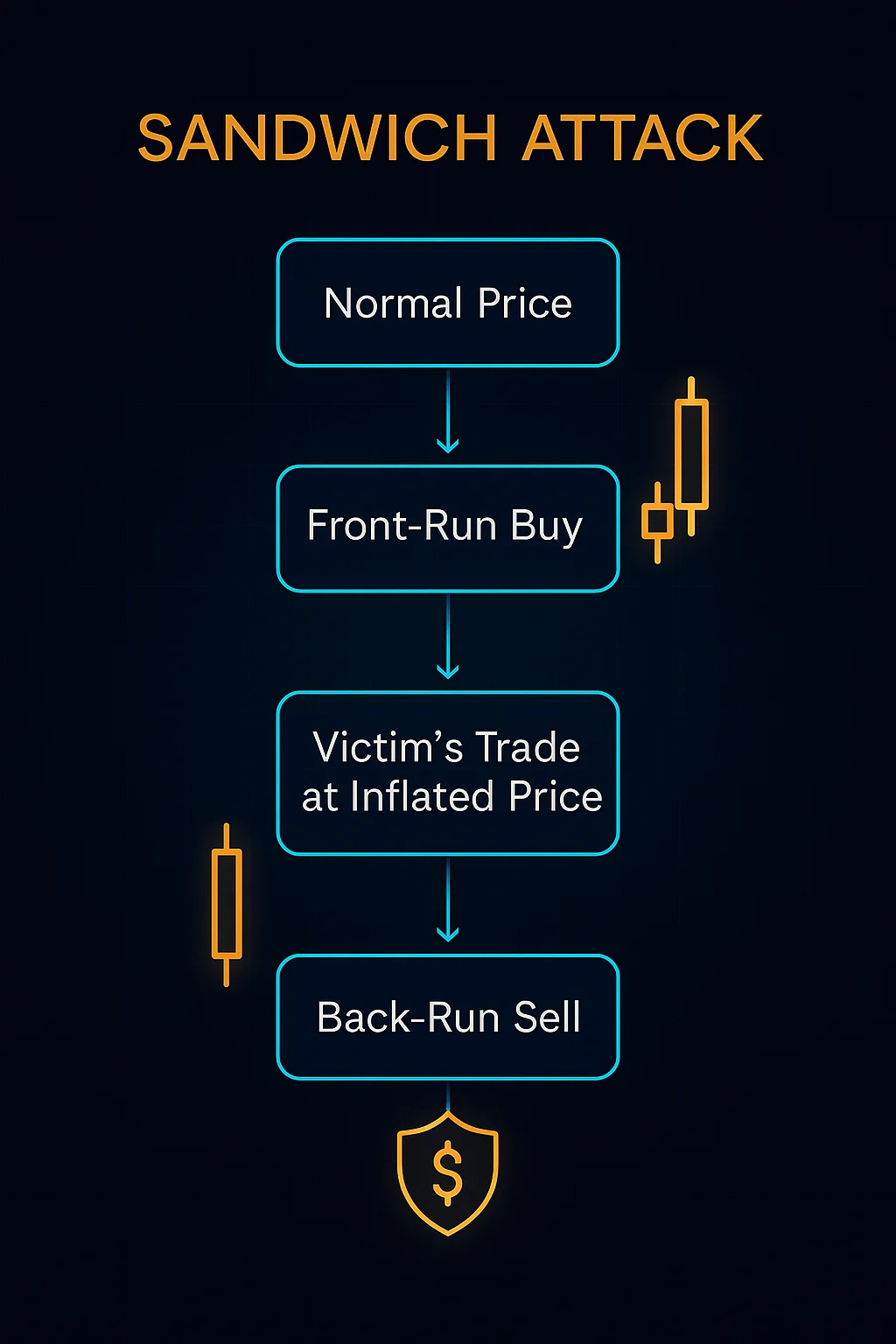
Sandwich attacks place trades before and after your transaction to manipulate prices and extract profit from your slippage. It’s like cutting in line twice – once in front of you and once behind you.
A sandwich attack involves placing a buy order immediately before a victim’s trade and a sell order immediately after to profit from the artificial price movement created by the victim’s transaction. The attacker extracts value through manipulated slippage.
How Sandwich Attacks Work
Front-running places a large buy order ahead of the victim’s purchase, artificially inflating the price before the victim’s transaction executes.
Back-running immediately sells the tokens at the inflated price after the victim’s purchase completes, capturing profit from the temporary price increase.
MEV extraction occurs as the attacker benefits from privileged information about pending transactions while the victim pays higher prices due to artificial slippage.
Real-World Examples
- DEX trading on Uniswap and other AMMs frequently faces sandwich attacks during periods of high gas prices
- Large swaps are particularly vulnerable as they create more price impact for attackers to exploit
- MEV bots automatically detect profitable sandwich opportunities in mempool data
Why Beginners Should Care
Hidden tax on DeFi trading that can add 1-5% to transaction costs beyond visible slippage and gas fees, significantly impacting returns.
Protection strategies include using MEV-protected RPCs, private mempools, or protocols specifically designed to prevent sandwich attacks.
Market impact reduces overall DeFi efficiency as users pay more for trades while value gets extracted by sophisticated MEV operators.
Related Terms: MEV, Front-Running, Slippage, Back-Running
