Sybil Attack
Sybil Attack: Fake Identity Manipulation
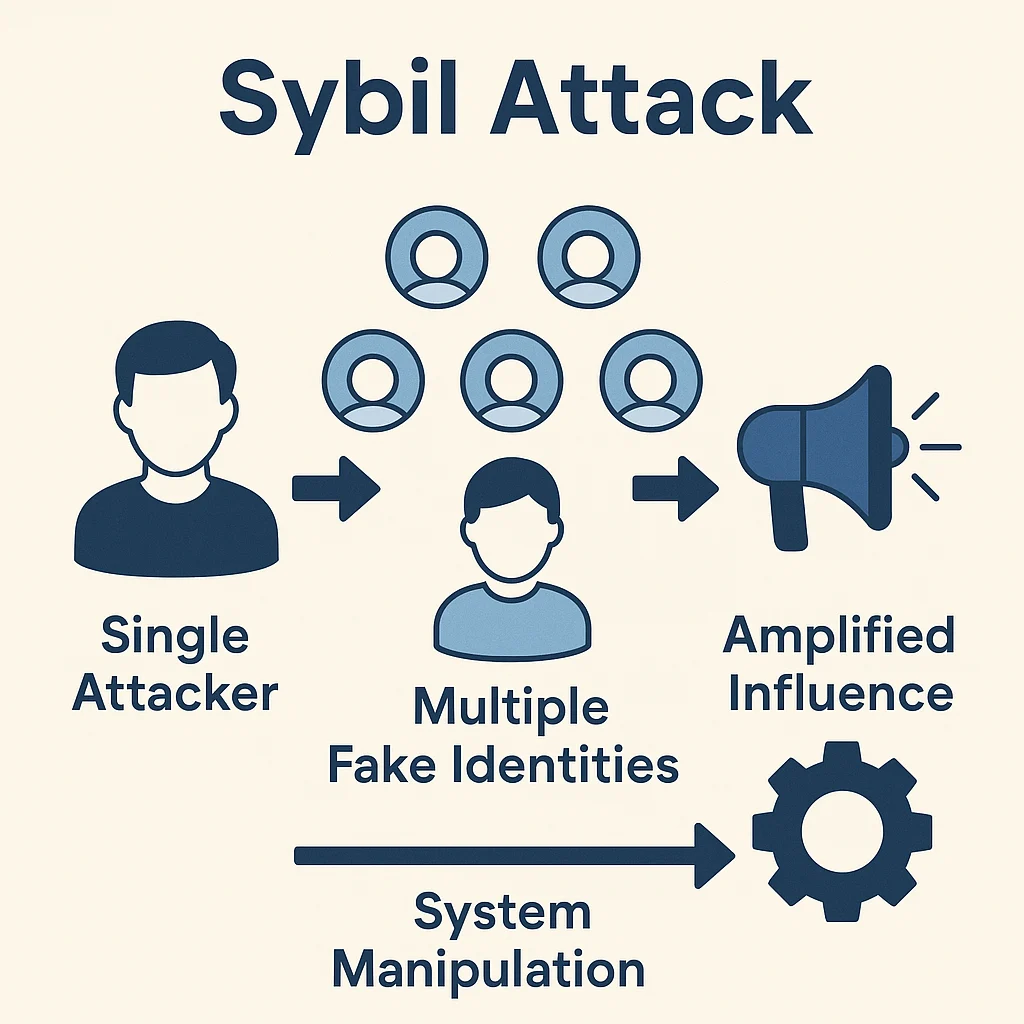
Sybil attacks involve creating multiple fake identities to gain disproportionate influence in networks that assume one person equals one vote. It’s like stuffing the ballot box with imaginary voters.
A Sybil attack is when an individual or entity creates multiple fake identities to gain unfair influence over a network, voting system, or resource allocation mechanism. These attacks exploit systems that rely on identity-based participation without proper verification.
How Sybil Attacks Work
Identity proliferation involves creating numerous fake accounts, wallets, or profiles to appear as many different participants in the system.
Influence amplification uses multiple identities to vote multiple times, claim multiple rewards, or gain disproportionate network power.
Detection evasion requires making fake identities appear legitimate through activity patterns, social connections, or other verification requirements.
Real-World Examples
- Airdrop farming using multiple wallets to claim the same airdrop many times
- Governance attacks creating multiple voting accounts to influence DAO decisions
- Review manipulation using fake accounts to boost ratings or reputation scores
Why Beginners Should Care
System integrity depends on preventing Sybil attacks to maintain fair participation and democratic decision-making processes.
Detection mechanisms like proof of humanity, stake-weighting, or social verification help identify and prevent fake identities.
Participation fairness ensures that resources and influence are distributed based on legitimate participation rather than identity manipulation.
Related Terms: Anti-Sybil Mechanism, Proof of Humanity, Governance Attack
