Wallet Drainer
Wallet Drainer: Malicious Fund Extraction
Wallet drainers are malicious smart contracts or applications designed to steal all assets from connected wallets through deceptive transaction approvals. They’re digital pickpockets with smart contract superpowers.
A wallet drainer is malicious software that tricks users into signing transactions that grant unlimited access to their cryptocurrency holdings. These attacks often disguise themselves as legitimate applications or NFT mints to gain user trust.
How Wallet Drainers Work
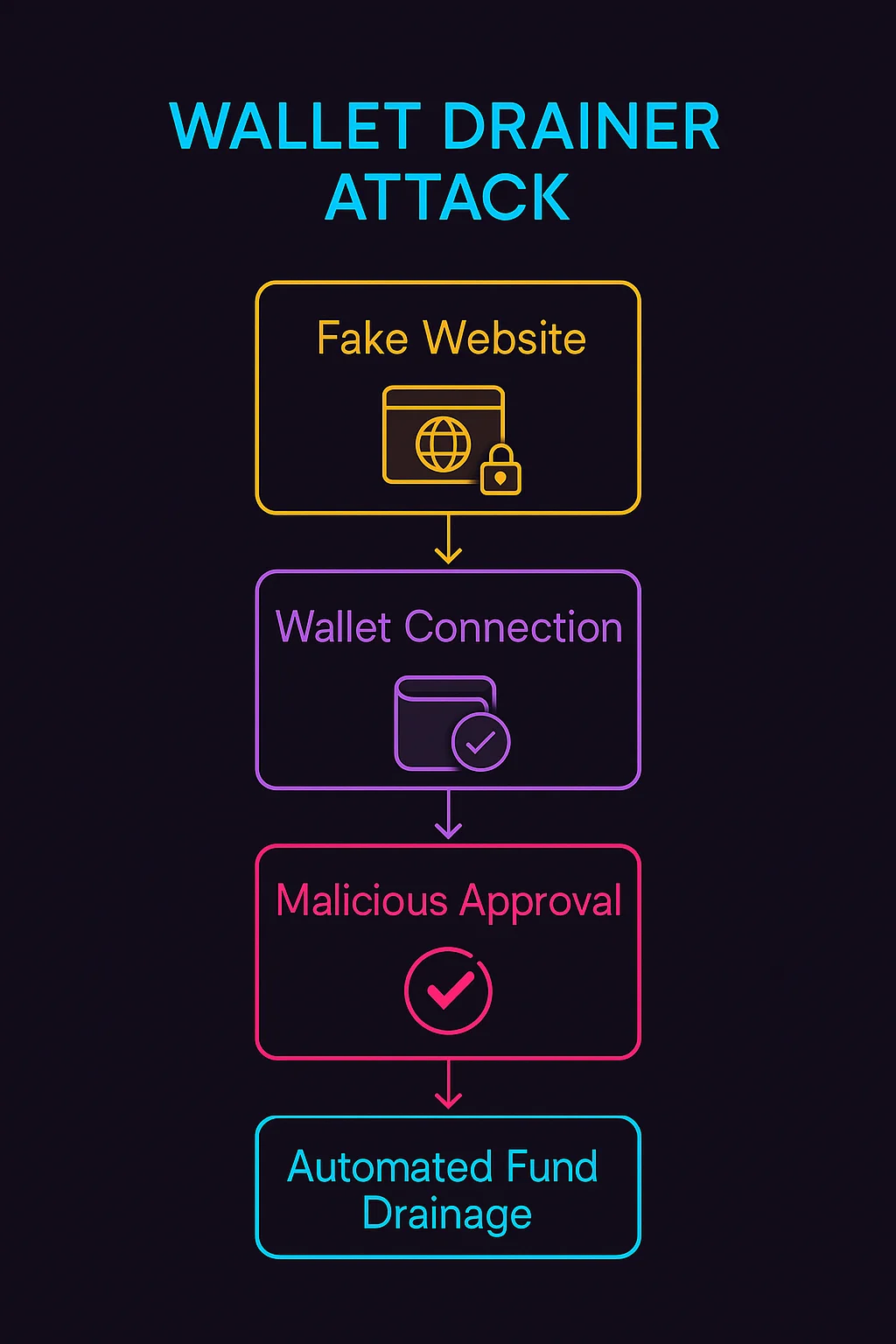
Social engineering presents fake websites, NFT mints, or airdrops that appear legitimate to trick users into connecting their wallets.
Malicious approvals request permissions that seem reasonable but actually grant unlimited access to users’ token holdings across multiple assets.
Automated extraction immediately drains approved tokens once users sign the malicious transactions, often faster than users can realize what happened.
Real-World Examples
- Fake NFT mint sites that drain wallets when users attempt to mint seemingly legitimate collections
- Phishing websites mimicking popular DeFi protocols to steal user approvals
- Malicious browser extensions that inject drainer code into legitimate websites
Why Beginners Should Care
Irreversible losses since blockchain transactions cannot be reversed once confirmed, making wallet drainer attacks permanently damaging.
Prevention strategies include carefully verifying website URLs, understanding transaction approvals, and using hardware wallets for additional security.
Growing sophistication as drainer attacks become more convincing and harder to detect, requiring increased vigilance from all crypto users.
Related Terms: Phishing Attack, Transaction Approval, Social Engineering, Hardware Wallet
